From Siloed Tools to Cohesive Resilience: Architecting Server, SSL & CDN Around Your Business Core
It’s 3 AM in the operations center. The CTO of a growing SaaS platform stares at three separate dashboards. His dedicated server cluster hums along at a comfortable 45% utilization. His CDN bill, however, is screaming 120% over budget for the third consecutive month. A third monitoring tab flashes a warning: the SSL certificate for a critical payment API subdomain expires in 72 hours. His team has followed every "best practice" for each individual technology, yet the company is paying a 30% annual premium in unnecessary costs and hidden inefficiencies simply because these tools don't talk to each other.
This scenario reveals the silent tax of the modern tech stack: we master individual components but fail at systems thinking. Your powerful server, your robust SSL/TLS setup, and your global CDN are not three independent line items. They are—or should be—three interlocking gears in a single machine designed for one purpose: to deliver your business outcomes reliably, securely, and efficiently.
The highest form of technical leadership today isn't about optimizing each piece to its theoretical limit. It's about architecting them into a cohesive, resilient system where the whole becomes vastly more capable than the sum of its isolated, over-optimized parts.
The High Cost of Silos: When "Best Practice" Creates Systemic Weakness
We operate in an age of abundant "best practices." Ops hardens the server. Security mandates the strictest TLS protocols. Networking deploys an intelligent, global CDN. Each decision is defensible in a vacuum, but combined, they can create a negative synergy that undermines your very goals.
Consider this real-world failure pattern: The security team, pursuing an impeccable audit score, configures the origin server to accept only TLS 1.3. A textbook best practice. Meanwhile, the infrastructure team has not updated the CDN configuration to use a compatible cipher suite for its origin pull connections. The result? A subset of the CDN's global edge nodes fails to connect to the origin, causing sporadic but persistent outages for users in specific regions. Security was enhanced, but availability—the most fundamental requirement—was broken.
Beyond outages lies the budget black hole. Fearing traffic spikes, you over-provision server capacity (Compute). Simultaneously, to protect that now-expensive origin, you purchase premium CDN features like "full-site caching" and "advanced bot mitigation." In reality, a more intelligent use of your server's spare capacity for dynamic assembly and smarter caching could reduce reliance on those costly CDN add-ons. You end up paying twice for overlapping capabilities, a direct result of siloed decision-making.
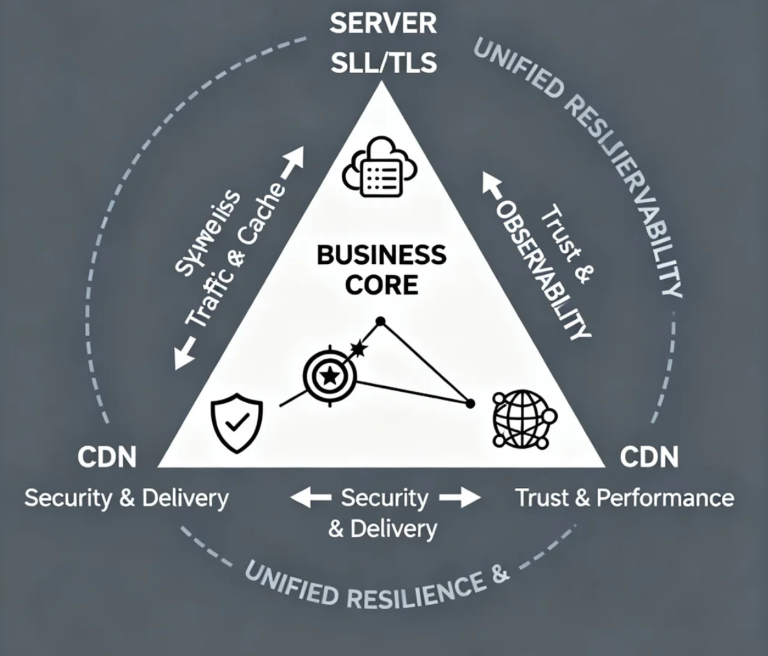
The Resilience Triangle: A Model for Cohesive Architecture
To escape this trap, you need a fundamental mental model: The Resilience Triangle. Place your core business objective—be it transaction completion, user onboarding, or media delivery—at the center. The three vertices are Server, SSL/TLS, and CDN. Their job is not to excel individually, but to interact in dynamic balance to protect and propel that center.
The Dynamics of the Triangle:
Server (The Source): Represents control, computational density, and data sovereignty. It evolves for depth and efficiency.
CDN (The Network): Represents scale, edge intelligence, and the user's first touchpoint. It evolves for breadth and awareness.
SSL/TLS (The Trust Layer): Represents authority, privacy, and protocol modernity. It evolves for trust and connection efficiency.
Every decision at one vertex must be stress-tested against the other two. Planning to migrate servers to a lower-cost region? You must evaluate: 1) The new latency's impact on CDN origin pull performance, and 2) Any regional compliance implications for your EV SSL certificate issuance. This is the shift from buying tools to designing an ecosystem.
The Strategic Pivot: Cost Migration, Not Just Cost Cutting
Financially, these three are often separate budget lines, reinforcing the illusion they are separate concerns. The transformative insight is understanding the powerful cost migration and value compensation between them.
A critical strategy is to shift expense from high-margin cost centers to low-margin ones. Overage bandwidth from your cloud provider is notoriously expensive. A premium CDN's bandwidth, due to its immense scale and peering, can be a fraction of the cost. Therefore, a primary architectural goal should be to engineer your CDN caching and rules to terminate 95%+ of requests at the edge. You're not cutting your server budget; you're migrating bandwidth spend to a more efficient provider, gaining global performance as a bonus.
The reverse is equally true. Investing in server-side efficiencies—like optimized API responses and advanced compression (Brotli)—directly reduces egress traffic and compute load on your CDN. Similarly, the brand trust and increased conversion rates driven by a properly deployed EV SSL certificate can generate revenue that offsets strategic investments in both server and CDN capabilities. View your infrastructure budget not as a cost, but as a portfolio of investments with non-linear business returns.
Cohesion Failures: Why 1+1+1 Can Be Less Than 2
An uncoordinated architecture doesn't just fail to add up; it actively subtracts. Here are the most common failure modes:
Failure Mode 1: The Redundant Security Tax.
You run a robust Web Application Firewall (WAF) on your server and enable a similar WAF on your CDN. This seems like "defense in depth," but it forces every legitimate user request through two independent sets of rule matching, JavaScript challenges, and latency. You can easily add 300+ milliseconds of unnecessary delay. Cohesion means defining clear boundaries: Let the CDN handle global rate-limiting, DDoS mitigation, and bulk threat filtering. Let the server-side WAF specialize in granular, application-layer logic protection. They should share intelligence, not duplicate work.
Failure Mode 2: The Protocol Disconnect.
Your origin server is cutting-edge, speaking only HTTP/2 and HTTP/3 (QUIC). Your CDN, however, is configured to communicate with users only over HTTP/2. This means users on poor mobile networks—who would benefit most from QUIC's faster handshake and resilience to packet loss—never get the upgrade. You must manage the protocol stack as a continuous chain from user to origin, ensuring both the "user-to-edge" and "edge-to-origin" links support and negotiate the optimal, compatible protocols.
Failure Mode 3: The Observability Black Hole.
When a user reports an error, your team must hop between consoles: CDN analytics for cache/hit status, server logs for application errors, and certificate monitors for validity. These data silos make it impossible to reconstruct the true journey of a single request. A cohesive architecture demands end-to-end context propagation. A unique Trace ID must be injected at the CDN edge, carried faithfully to the origin, and stamped on every log entry. This creates a single, queryable story for every transaction.
Your Four-Step Blueprint for Cohesive Resilience
Moving from theory to practice requires a deliberate framework.
Step 1: The Cohesion Audit & Goal Alignment.
Gather leads from infrastructure, networking, security, and product. Ask: 1) What is our top-priority business outcome this quarter? (e.g., "Improve checkout conversion in Europe.") 2) What is each component—Server, SSL, CDN—individually doing to advance this goal? 3) Where are the visible handoffs, gaps, or conflicts between them? The answers will instantly illuminate your biggest cohesion breaks.
Step 2: Define Unified "Resilience SLOs."
For a critical user journey (e.g., "Search to Purchase"), define a Service Level Objective that spans all three pillars. Example: "99% of user journeys must complete with end-to-end latency < 2 seconds, zero SSL validation errors, and with ≥90% of component requests served from CDN cache or edge logic." This single SLO forces joint design, measurement, and accountability.
Step 3: Implement Key Technical Linkages.
Configuration Sync: Bind CDN origin pull settings (timeouts, protocols) directly to server application and SSL configurations.
Security Orchestration: Automate the flow of threat intelligence; have the CDN dynamically update origin server block lists or rate-limiting rules.
Unified Observability: Mandate that the CDN passes core context (
X-Request-ID, user country) to the origin and that all logs aggregate into a single platform that can correlate CDN events with application traces.
Step 4: Create a Joint Capacity & Cost Model.
Build a single financial and capacity model that includes all three elements. Simulate growth: if user traffic increases by 40%, does the most efficient path involve scaling server CPU, tuning CDN caching rules, or optimizing TLS handshake overhead? This model shifts budgeting from "padding three separate silos" to purchasing elastic capacity for the unified system.
When your Server, SSL, and CDN cease to be three separate bills and three different logins, and instead function as a single, integrated resilience engine, a fundamental change occurs. Your team's focus shifts from reacting to component-level alerts to proactively optimizing the energy efficiency of the entire system.
You stop asking, "Why is the CDN bill so high?" and start asking, "How can we adjust our caching strategy to improve user experience and reduce our total infrastructure spend by 15% next quarter?" You no longer debate "which SSL certificate to buy," but know decisively that "deploying an EV certificate on our core domain and enforcing TLS 1.3 via CDN will increase trust and directly impact conversion."
This is the journey from siloed tools to cohesive resilience. It begins with recognizing the invisible fractures between your technology purchases. It is achieved by intentionally weaving them into a living system that breathes in sync with the heartbeat of your business. Your ultimate competitive advantage will no longer stem from any single technology's prowess, but from the unique, unbreakable resilience of the whole. It's time to architect not just for function, but for orchestrated strength.

